x64dbg

An open-source binary debugger for Windows, aimed at malware analysis and reverse engineering of executables you do not have the source code for. There are many features available and a comprehensive plugin system to add your own. You can find more information on the blog!
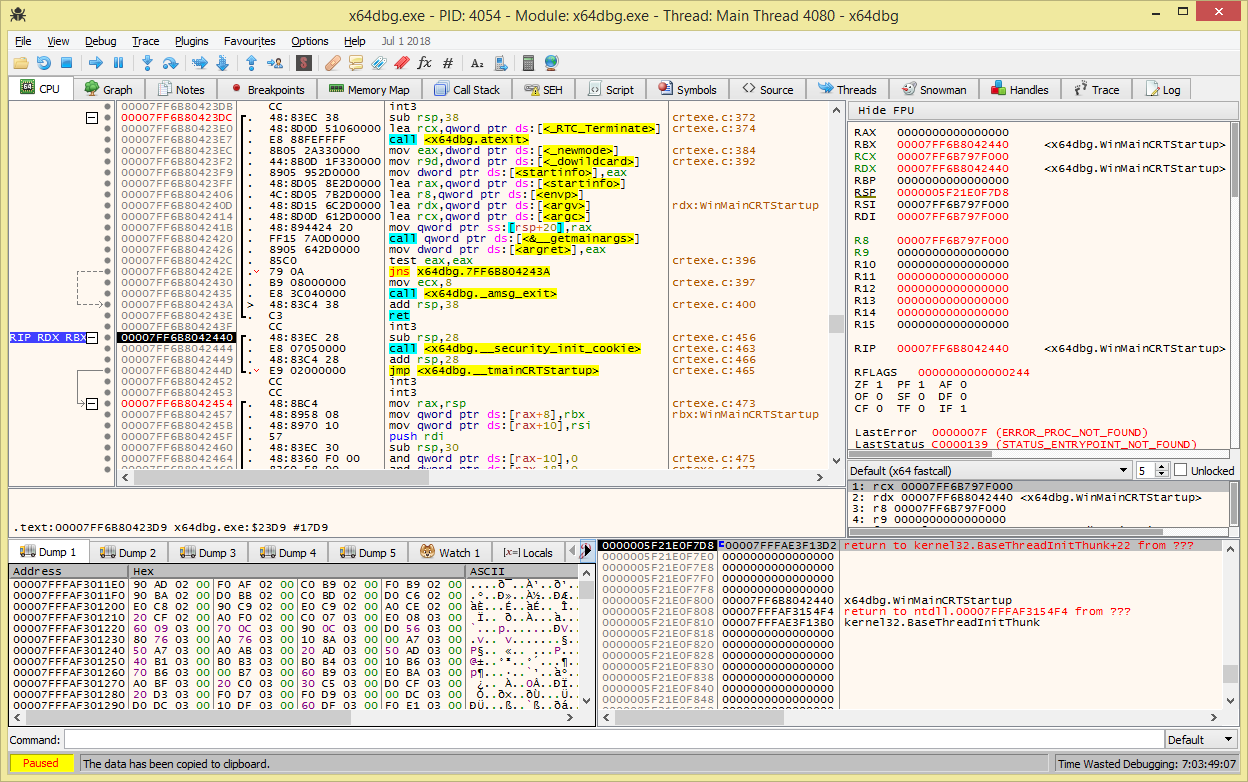
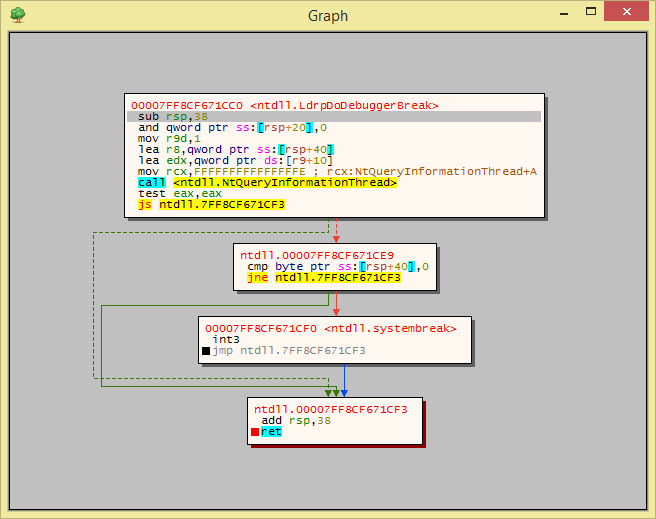
Screenshots
Installation & Usage
- Download a snapshot from GitHub, SourceForge or OSDN and extract it in a location your user has write access to.
- Optionally use
x96dbg.exeto register a shell extension and add shortcuts to your desktop. - You can now run
x32\x32dbg.exeif you want to debug a 32-bit executable orx64\x64dbg.exeto debug a 64-bit executable! If you are unsure you can always runx96dbg.exeand chose your architecture there.
You can also compile x64dbg yourself with a few easy steps!
Contributing
This is a community effort and we accept pull requests! See the CONTRIBUTING document for more information. If you have any questions you can always contact us or open an issue. You can take a look at the easy issues to get started.
Credits
- Debugger core by TitanEngine Community Edition
- Disassembly powered by Zydis
- Assembly powered by XEDParse and asmjit
- Import reconstruction powered by Scylla
- JSON powered by Jansson
- Database compression powered by lz4
- Bug icon by VisualPharm
- Interface icons by Fugue
- Website by tr4ceflow
Developers
Code contributions
You can find an exhaustive list of GitHub contributers here.
Special Thanks
- Sigma for developing the initial GUI
- All the donators!
- Everybody adding issues!
- People I forgot to add to this list
- Writers of the blog!
- EXETools community
- Tuts4You community
- ReSharper
- Coverity
- acidflash
- cyberbob
- cypher
- Teddy Rogers
- TEAM DVT
- DMichael
- Artic
- ahmadmansoor
- _pusher_
- firelegend
- kao
- sstrato
- kobalicek
- athre0z
- ZehMatt
Without the help of many people and other open source projects it would not have been possible to make x64dbg what is it today, thank you!